Githubusercontent token
Stolen and compromised credentials are the number one cause of data breaches across the industry, githubusercontent token. GitHub has a long history of protecting developers and enterprises from such threats with security efforts like making it easier for developers to adopt 2FA with the GitHub mobile app and robust webauthn supportand scanning for secrets at the point of push for Githubusercontent token Advanced Security customers. But safeguarding credentials perfectly is extremely difficult.
Log in. Sign up. JavaScript is disabled. For a better experience, please enable JavaScript in your browser before proceeding. Status Not open for further replies.
Githubusercontent token
GitHub admite actualmente dos tipos de personal access token: fine-grained personal access token y personal access tokens classic. GitHub recomienda usar un fine-grained personal access token siempre que sea posible, en lugar de personal access tokens classic. El Fine-grained personal access token tiene varias ventajas de seguridad con respecto a los personal access tokens classic :. Los Personal access tokens classic son menos seguros. Si estas opciones no son posibles, y debes crear un personal access token, considera el uso de otro servicio de CLI para almacenar el token de forma segura. Para dejar comentarios, consulta el debate sobre los comentarios. En Propietario del recurso , selecciona un propietario del recurso. En Acceso al repositorio , selecciona los repositorios a los que quieres que acceda el token. Si elegiste Solo repositorios seleccionados en el paso anterior, en la lista desplegable Repositorios seleccionados , elige los repositorios a los que quieres que acceda el token. Nota : Tu personal access token classic puede acceder a todos los repositorios a los que tengas acceso. Opcionalmente, para copiar el nuevo token al portapapeles, haz clic en. Debes eliminar un personal access token si ya no es necesario. A la derecha del personal access token que quieras eliminar, haz clic en Eliminar. Skip to main content. Seguridad de la cuenta.
Eventos de registro de seguridad. Top Contributors this Month View All.
.
OpenID Connect allows your workflows to exchange short-lived tokens directly from your cloud provider. Before the workflow can access these resources, it will supply credentials, such as a password or token, to the cloud provider. These credentials are usually stored as a secret in GitHub, and the workflow presents this secret to the cloud provider every time it runs. However, using hardcoded secrets requires you to create credentials in the cloud provider and then duplicate them in GitHub as a secret. With OpenID Connect OIDC , you can take a different approach by configuring your workflow to request a short-lived access token directly from the cloud provider. Your cloud provider also needs to support OIDC on their end, and you must configure a trust relationship that controls which workflows are able to request the access tokens. By updating your workflows to use OIDC tokens, you can adopt the following good security practices:. The following diagram gives an overview of how GitHub's OIDC provider integrates with your workflows and cloud provider:. When the job runs, the OIDC token is presented to the cloud provider. To validate the token, the cloud provider checks if the OIDC token's subject and other claims are a match for the conditions that were preconfigured on the cloud role's OIDC trust definition.
Githubusercontent token
That file is from a private repository in an Organization using SSO. When I try to fetch a file from a private repository, only the call using the PAT works:. Is it something even possible? The OAuth application that I registered at the start of this post is for Keycloak. A user can authenticate to my application using GitHub as the identity provider. Once authenticated, Keycloak stores the token returned by GitHub and the user can retrieve it on demand to access files in GitHub.
Resultado dodgers hoy
This does have some trade-offs, though, which are detailed in the next section. There is likely additional authentication data stored in the request headers so the token alone isn't enough to compromise the file. Firmar etiquetas. They have access to all of the repositories and organizations that the user could access, and are allowed to live forever. Modo sudo. Eventos de registro de seguridad. Permiso denegado para otro repositorio. Acerca de SSH. As the resources are hosted and managed by different software, the two softwares github. Solucionar problemas de SSH.
Before proceeding, you must plan your security strategy to ensure that access tokens are only allocated in a predictable way.
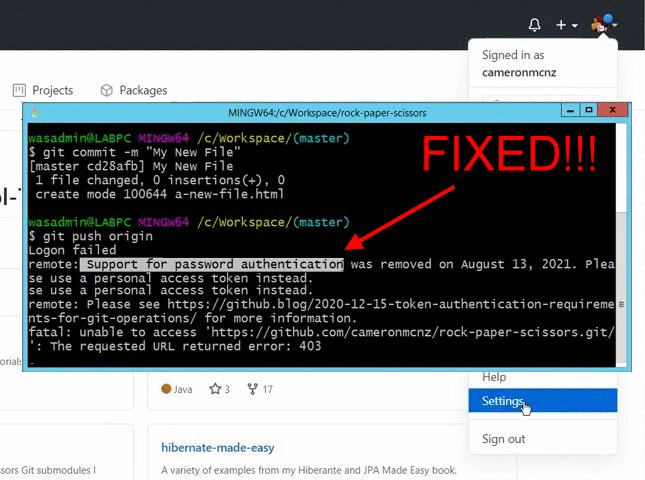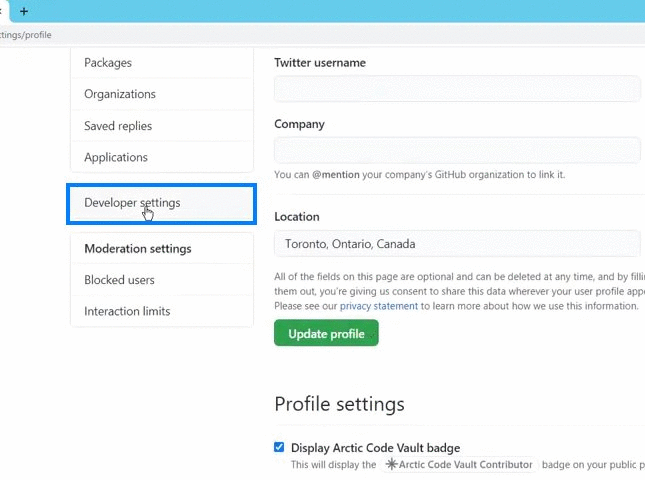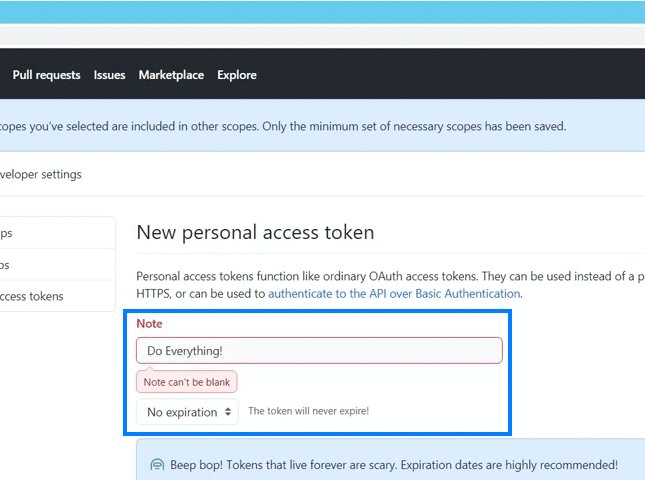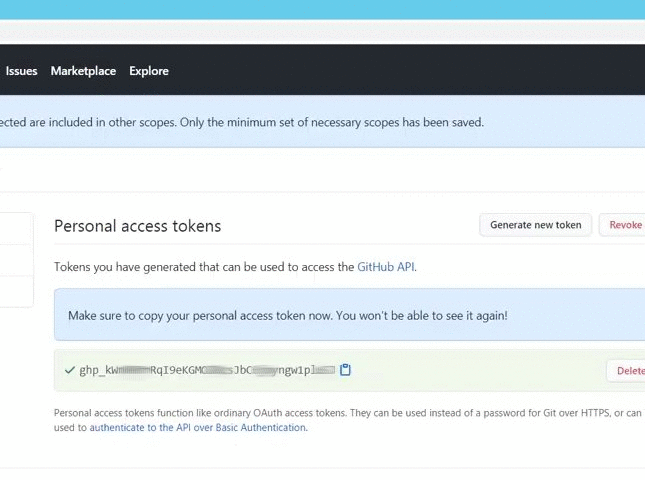
Los Personal access tokens classic son menos seguros. Skip to main content. Is there any way to remove the 'token'? But safeguarding credentials perfectly is extremely difficult. Log in. You can give that feedback via this dedicated discussion forum. Enterprise Owners can also set policies across their Organizations via the new Personal access tokens page in the Policies tab. Until now, personal access tokens PATs have only provided very coarse-grained permissions. This option is enabled by default. As an example, you can now create a PAT that can only read issues and do nothing else — not even read the contents of a repository. Claves SSH eliminadas o faltantes. Revisar tus claves SSH. Enterprise Owners can also set policies across their Organizations via the new Personal Access Tokens page in the Policies tab. Personal access tokens classic are given permissions from a broad set of read and write scopes.

0 thoughts on “Githubusercontent token”