Bloodhound github
This version of BloodHound, bloodhound github. For BloodHound CE, check out the bloodhound-ce branch. You can install the ingestor via pip with pip install bloodhoundor by cloning this repository and running pip install. The installation bloodhound github add a command line tool bloodhound-python to your PATH.
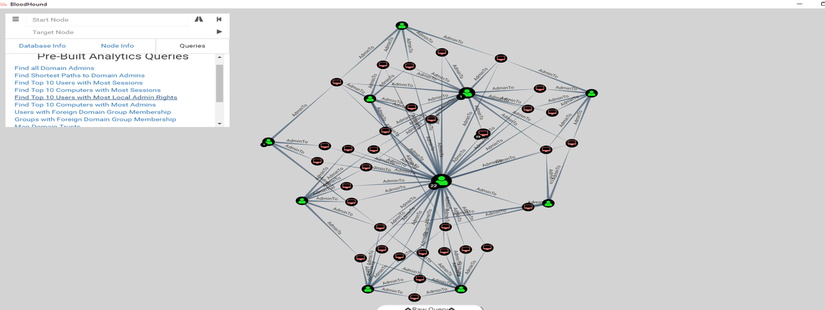
BloodHound is a monolithic web application composed of an embedded React frontend with Sigma. It is deployed with a Postgresql application database and a Neo4j graph database, and is fed by the SharpHound and AzureHound data collectors. BloodHound uses graph theory to reveal the hidden and often unintended relationships within an Active Directory or Azure environment. Attackers can use BloodHound to easily identify highly complex attack paths that would otherwise be impossible to identify quickly. Defenders can use BloodHound to identify and eliminate those same attack paths.
Bloodhound github
Full Changelog : v4. Full Changelog : 4. Rolling release of BloodHound compiled from source 0d This release contains several fixes for AzureHound, as well as fixes for searching and viewing azure nodes. Big thanks to everyone who submitted PRs and fixes cnotin jtothef nheineger Scoubi. This is a major feature release for BloodHound, including support for Azure attack primitives in the attack graph with new nodes and edges. For information on changes in this version, please refer to Andy Robbins' blog post about the release of AzureHound. Skip to content. You signed in with another tab or window. Reload to refresh your session. You signed out in another tab or window. You switched accounts on another tab or window.
Arrrrooooooooo What's Changed Brand new SharpHound, bloodhound github, rewritten from the ground up for better performance and data consistency -SearchForest is back baby!
To get started with BloodHound, check out the BloodHound docs. BloodHound is a single page Javascript web application, built on top of Linkurious , compiled with Electron , with a Neo4j database fed by a C data collector. BloodHound uses graph theory to reveal the hidden and often unintended relationships within an Active Directory or Azure environment. Attackers can use BloodHound to easily identify highly complex attack paths that would otherwise be impossible to quickly identify. Defenders can use BloodHound to identify and eliminate those same attack paths. Both blue and red teams can use BloodHound to easily gain a deeper understanding of privilege relationships in an Active Directory or Azure environment.
To get started with BloodHound, check out the BloodHound docs. BloodHound is a single page Javascript web application, built on top of Linkurious , compiled with Electron , with a Neo4j database fed by a C data collector. BloodHound uses graph theory to reveal the hidden and often unintended relationships within an Active Directory or Azure environment. Attackers can use BloodHound to easily identify highly complex attack paths that would otherwise be impossible to quickly identify. Defenders can use BloodHound to identify and eliminate those same attack paths. Both blue and red teams can use BloodHound to easily gain a deeper understanding of privilege relationships in an Active Directory or Azure environment. BloodHound is maintained by the BloodHound Enterprise team.
Bloodhound github
BloodHound is a monolithic web application composed of an embedded React frontend with Sigma. It is deployed with a Postgresql application database and a Neo4j graph database, and is fed by the SharpHound and AzureHound data collectors. BloodHound uses graph theory to reveal the hidden and often unintended relationships within an Active Directory or Azure environment. Attackers can use BloodHound to easily identify highly complex attack paths that would otherwise be impossible to identify quickly. Defenders can use BloodHound to identify and eliminate those same attack paths. Both blue and red teams can use BloodHound to easily gain a deeper understanding of privilege relationships in an Active Directory or Azure environment. The easiest way to get up and running is to use our pre-configured Docker Compose setup.
Obt spider
Go to file. Get SharpHound. Packages 0 No packages published. Pre-Compiled BloodHound binaries can be found here. You can install the ingestor via pip with pip install bloodhound , or by cloning this repository and running pip install. Last commit date. About BloodHound Enterprise. MIT license. Go to file. Latest commit. Custom properties. All reactions.
Full Changelog : v4.
You signed in with another tab or window. Custom properties. Report repository. Reload to refresh your session. Packages 0 No packages published. Releases 12 v2. You can install the ingestor via pip with pip install bloodhound , or by cloning this repository and running pip install. You signed out in another tab or window. Releases 13 tags. Defenders can use BloodHound to identify and eliminate those same attack paths. SharpHound must be run from the context of a domain user, either directly through a logon or through another method such as RUNAS. May 23, Reload to refresh your session. Full Changelog : v4. Notifications Fork 1.

Excuse for that I interfere � I understand this question. I invite to discussion.
In my opinion you are not right. Write to me in PM, we will talk.
So simply does not happen