Picoctf
You are going to have real fun here. And, picoctf, you will gain the ability picoctf do impressive things in life using a computer. It will be like acquiring a superpower to be able to do things that ordinary people cannot do, picoctf.
Gain knowledge about introductory through advanced level cybersecurity principles in our noncompetitive features the picoGym and the picoPrimer. Build your CTF skills, help yourself advance your personal best score, and prepare for the big show using our mini Competitions to practice. See yourself in a career in cybersecurity. Cybersecurity skills are in high demand in the workforce and the need grows as computers continue to be an integral part of everyday life. Monitor student or group progress when using the Classroom feature.
Picoctf
.
When we want to hide a message, picoctf, we say that we encrypt the message.
.
Participants 13 years and older of all skill levels are encouraged to compete. Competitors must reverse-engineer, break, hack, decrypt, and think creatively and critically to solve the challenges and capture the digital flags. Competition prizes have eligibility requirements, but everyone is encouraged to play for fun and learning. Be at least 13 years old if under 18, have consent of parent or legal guardian to participate. Prizes and awards may have requirements. See full competition rules for details.
Picoctf
If you do not agree with these terms and conditions as stated, your only recourse is to discontinue using and participating in the Competition. CMU shall have the right to modify these Competition Rules at any time, which modification shall be effective immediately upon posting. Accordingly, we suggest that you check review our Competition Rules when you use the Services to stay informed.
Yurtdışı öğretmenlik yaş sınırı
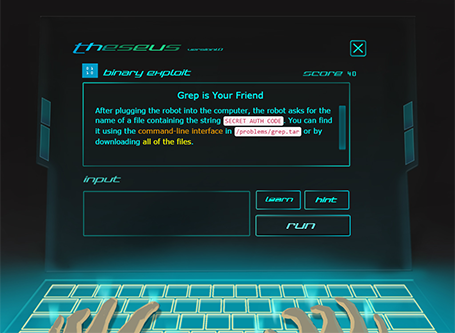
The following is an example in PHP:. This directory has a file, called. If one bit of the file was changed, you would get a very different hash. For example, create a new file called "bio2. That allows us to wrap around a number, because it calculates the remainder of the division. When you call a program from the command line, it is possible to pass arguments in the same way you do with several programs in the terminal. To use cryptography in real life, you should never use your own implementations. But now, we want to look at specific directories so we will need their inodes. Application layer: Responsible for handling data traffic between applications. It will show the same message. The cybersecurity topics in picoCTF include introductory level concepts progressing to mastery level.
Welcome, future cybersecurity enthusiasts! This walkthrough is tailored for beginners, including kids, who are new to CTFs. We'll explore the basics, provide step-by-step instructions, and highlight key concepts along the way.
Having those to values, you are be able to calculate the private key. Nowadays, there are computers everywhere. This causes a problem because it leaks structure in the encrypted text. In this particular text, you should get:. Now, if we print the variable, it should print "Hello World! The step by step walkthrough is more for learners who have never ventured in a particular task before. The mac address is used for this layer. Another element we add in this operation mode, is that we do not encrypt blocks independently, but we use the encrypted text from one block and XOR it with the next block of cleartext we want to encrypt. To filter out ARP messages, add! For example, if we have the string "hello" and the integer , and we want to create a string that is "hello", we can concatenate those two values. It takes some practice to get used to, but it is worth the time as it probably cuts number of key presses in half! Suppose you want to communicate secretly with asymmetric crypto. Put that statement in the SQL editor and hit the button "Run".

I apologise, but, in my opinion, you are not right. Let's discuss. Write to me in PM, we will talk.