Iot ssh over ssh
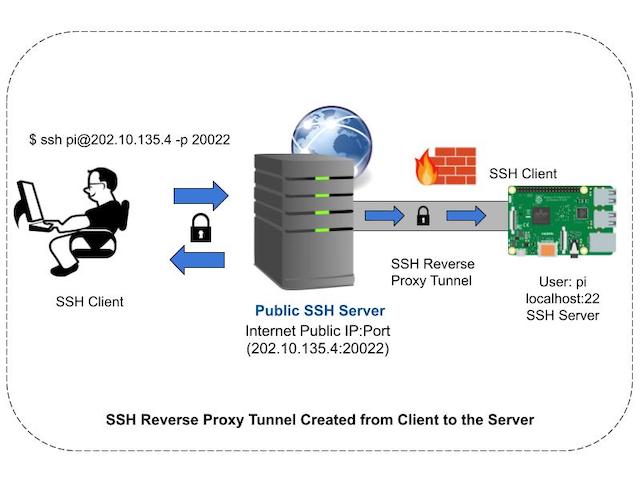
Reverse SSH tunneling is a technique used to establish a secure connection from a remote server or a remote IoT device back to a local machine. Instead of iot ssh over ssh from a local machine to a remote server, as in traditional SSH connections, reverse SSH tunneling establishes a connection from the remote server to the local machine. This is not a very difficult thing to do and it relies on the ssh tool available in basically any operating system.
Thankfully, you can navigate around this by setting up an SSH tunnel. This is widely used in and outside of the IoT community. Is there an even better solution for IoT devices? Book a consultation today and get help with tech support, business inquiries, and other IoT queries. We are happy to help. Talk to you soon. It uses a network port to create a connection session between the server — that listens on the chosen port — and the client — which sends an SSH request on that port.
Iot ssh over ssh
These tips will help you safeguard your IoT and keep it safe from unauthorized access. Here are some security considerations to keep in mind when using SSH for remote access to your IoT device:. It is critical to change the default password to a strong and unique one as soon as possible to prevent unauthorized access. Use strong authentication credentials: Use strong and unique usernames and passwords for all user accounts on your IoT device, including the regular user account you use to log in via SSH. Avoid using easily guessable usernames or weak passwords, and consider using a password manager to generate and store complex passwords securely. This includes installing security updates and patches for the OS and SSH software as they become available. A Use SSH key-based authentication : Instead of relying solely on password-based authentication, it is recommended to use SSH key-based authentication, which is more secure. Then disable password-based authentication in SSH configuration to prevent brute-force attacks. Follow SSH key management best practices and understand its limitations. B While SSH key-based authentication is better and stronger than the password based authentication, it is not free from its own caveats and limitations such as SSH key sprawl and infinite validity. This adds an additional layer of security and prevents unauthorized access to your SSH keys, even if they are compromised.
SocketXP solution works without making any changes to your WiFi router settings.
In these tutorials, you'll learn how to remotely access a device that's behind a firewall. You can't start a direct SSH session into the device because the firewall blocks all inbound traffic. The tutorials show you how you can open a tunnel and then use that tunnel to start an SSH session to a remote device. The prerequisites for running the tutorial can vary depending on whether you use the manual or quick setup methods for opening a tunnel and accessing the remote device. For information about prerequisites for the quick setup method tutorial, see Prerequisites for quick setup method. For information about prerequisites for the manual setup method tutorial, see Prerequisites for manual setup method. If you use this setup method, you must configure the local proxy on your source device.
With the ability to connect and control devices from anywhere in the world, IoT technology has brought convenience and efficiency to our daily lives. However, with this increased connectivity comes the need for secure remote access to these devices. By the end of this article, you will have a better understanding of how to use SSH to securely access your IoT devices over the internet from outside network. SSH stands for Secure Shell, which is a cryptographic network protocol for secure remote access to devices over an unsecured network such as the internet. SSH uses encryption to secure the connection between two devices. It creates a secure tunnel through which data can be transmitted and received. You need to download, install and setup SSH server in your IoT device so that you could connect to it remotely via the internet. SSH allows for remote management and monitoring of these devices from anywhere in the world. By using SSH, users can securely access their IoT devices and perform tasks such as updating firmware, changing settings, and troubleshooting issues.
Iot ssh over ssh
SSH makes accessing remote IoT devices securely possible, but keeping client-server connections private requires careful management and proper configuration. IoT devices offer automation, efficiency, and convenience, but leaving them unmonitored can open up avenues of vulnerability. In business settings, IoT remote access is key to maintaining and monitoring IoT activity in real time to ensure safe use. Yet, common shortcuts and risky backend methods can lead cybercriminals straight into a bustling network. This guide will explain how to harness the SSH protocol to securely supervise IoT networks, keeping data confidential and people safe. IoT remote monitoring involves the surveillance of smart technology as they operate in tandem with each other. Typically, an administrator uses a software program or application to view the status of each IoT device from a centralized digital control center. From here, administrators can change machine settings, address malfunctions, and even log activity for auditing. For enterprises heavily reliant on hundreds of IoT devices to meet daily business objectives, remote monitoring helps save time and money that would otherwise be spent on in-person visits, extended downtime, and troubleshooting costs.
Microwars
SocketXP has no way to decrypt or eavesdrop your encrypted data without knowing your SSH private keys. After you create the tunnel, you can use an in-browser command line interface to SSH into the remote device. Besides preventing and resolving breaches before they can inflict harm, remote access to IoT devices builds on the capabilities that come with wireless interconnectivity. If you've got a moment, please tell us what we did right so we can do more of it. Investigate and take appropriate action upon any signs of potential security threats. For example, sensors and timers that shift traffic lights can be interrupted, potentially causing automobile accidents. SSH offers a suite of privileged access management PrivX solutions founded on zero trust and just-in-time architecture for one-time certificate use, preventing credential leaks that hackers exploit. Open a tunnel and use browser-based SSH to access remote device. Furthermore, it only requires minimal code changes. For both setup methods, you must allow outbound traffic on port Here are some security considerations to keep in mind when using SSH for remote access to your IoT device:. Looking for other Great posts?
You can use the quick setup or the manual setup method for creating a tunnel. This tutorial shows how to open a tunnel using the quick setup method and use the browser-based SSH to connect to the remote device. For an example that shows how to open a tunnel using the manual setup method, see Open a tunnel using manual setup and connect to remote device.
IoT remote monitoring involves the surveillance of smart technology as they operate in tandem with each other. Copy and paste the below single-touch installation command from the SocketXP Portal page on to the terminal of your IoT device. Here are some security considerations to keep in mind when using SSH for remote access to your IoT device:. Please email us at: [email protected]. Things supports password authentication and public key authentication. IoT devices offer automation, efficiency, and convenience, but leaving them unmonitored can open up avenues of vulnerability. Try our demo for Video Surveillance? So to gain remote access from the internet to IoT devices in your home or factory is not easy and straightforward. Keep backups and monitor for anomalies: Regularly back up your IoT device and monitor for any anomalies in system behavior or log files. For information about prerequisites for the quick setup method tutorial, see Prerequisites for quick setup method. The tutorials show you how you can open a tunnel and then use that tunnel to start an SSH session to a remote device. It allows internet traffic to travel between local and remote devices. Setting up this in real life is fairly straightforward if you work with open ports.

0 thoughts on “Iot ssh over ssh”