Cve score
CVE is a glossary that classifies vulnerabilities. A CVE score is often used for prioritizing the security of vulnerabilities, cve score.
Advisories, exploits, RSS feeds and various other vulnerability intelligence features have been added along with APIs, email alerts, feeds and more. We want to save our users from Googling for information! We want to make our users more efficient and productive by providing them with easy access to information and the necessary utilities. We want to become your one-stop shop for anything related to vulnerabilities. Instead of using 20 different tools and 50 web sites, you should only need CVEdetails.
Cve score
See NinjaOne in action! As we move into the new year, organizations can expect the number of cyberattacks to increase significantly. In order to battle these upcoming threats, effective patching and patch management processes will be essential. This glossary organizes these security weaknesses with identification numbers, dates, and descriptions. CVSS scores quantify the severity of vulnerabilities. An IT team can use this information to determine which vulnerabilities pose the most serious threats and resolve them first before moving on to more minor weaknesses. For example, a vulnerability with a CVSS score of 8 is more of a threat than a vulnerability with a score of 3. In this case, an IT team can resolve the vulnerability scored 8 first before resolving the less serious vulnerability scored 3. The CVE provides descriptions, dates, and other information about vulnerabilities. Additionally, the CVE sometimes lists the fixes or solutions for a specific vulnerability. This valuable information allows an IT team to learn more about a vulnerability so that they can come up with a solution. These assessments help an IT team to plan, prepare, and resolve vulnerabilities before they become serious issues for an organization. They allow IT teams to categorize, prioritize, and create order when dealing with pesky vulnerabilities.
As it is not possible to be confident that every cve score system has been fixed or patched, the temporal score cannot reduce below a certain level based on the vendor's actions, and may increase if an automated exploit for the vulnerability is developed. These organizations include research organizations, and security and IT vendors. Application Security, cve score.
CVSS helps organizations prioritize and coordinate a joint response to security vulnerabilities by communicating the base, temporal and environmental properties of a vulnerability. Vulnerable Software. Vendors Products Version Search. Vulnerability Intel. Attack Surface. These metric groups are described as follows: Base : represents the intrinsic and fundamental characteristics of a vulnerability that are constant over time and user environments. Temporal : represents the characteristics of a vulnerability that change over time but not among user environments.
CVE is a glossary that classifies vulnerabilities. A CVE score is often used for prioritizing the security of vulnerabilities. The CVE glossary is a project dedicated to tracking and cataloging vulnerabilities in consumer software and hardware. SCAP evaluates vulnerability information and assigns each vulnerability a unique identifier. The CVE glossary was created as a baseline of communication and source of dialogue for the security and tech industries. CVE identifiers serve to standardize vulnerability information and unify communication amongst security professionals.
Cve score
Official websites use. Share sensitive information only on official, secure websites. CVSS is not a measure of risk. The Base metrics produce a score ranging from 0 to 10, which can then be modified by scoring the Temporal and Environmental metrics. A CVSS score is also represented as a vector string, a compressed textual representation of the values used to derive the score. Thus, CVSS is well suited as a standard measurement system for industries, organizations, and governments that need accurate and consistent vulnerability severity scores.
Family search lds
We are here to make life easier for you. Patching and dealing with vulnerabilities is no easy task. The collateral damage potential CDP metric measures the potential loss or impact on either physical assets such as equipment and lives , or the financial impact upon the affected organisation if the vulnerability is exploited. Thus, if a published vulnerability provides no details about the vulnerability, NVD analysts will assess that vulnerability as a See updates and change log for more information. Usability was a prime consideration when making improvements to the CVSS standard. To find those, security personnel have to do some additional sleuthing. Business Email Required. Two common uses of CVSS are calculating the severity of vulnerabilities discovered on one's systems and as a factor in prioritization of vulnerability remediation activities. Specialised conditions exist, such as a race condition with a narrow window, or a requirement for social engineering methods that would be readily noticed by knowledgeable people. The Modified Base is intended to reflect differences within an organization or company compared to the world as a whole. NinjaOne is giving you a limited license to use the script in accordance with these legal terms. There is total loss of integrity; the attacker can modify any files or information on the target system. CVE is a glossary that classifies vulnerabilities. Start a Free Trial.
The Common Vulnerability Scoring System CVSS is a free and open industry standard for assessing the severity of computer system security vulnerabilities.
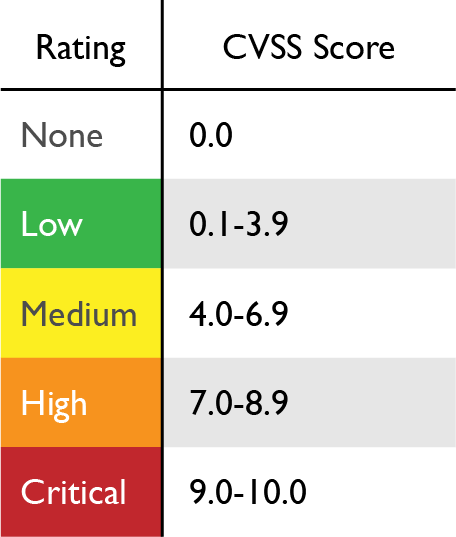
There is no solution available, or it is impossible to apply a suggested solution. To secure your house, you first need to know how many windows and doors you have attack surface , if your doors and windows are secured properly and if they can be opened due to some defects in your locks or similar vulnerability intelligence. Vulnerability Intel. Vendors can then report the vulnerability to a CNA along with patch information, if available. I work in These criteria includes:. Textual severity ratings of None 0 , Low 0. Existence of burglars in your neighbourhood or whether burglars are targeting specific lock types etc threat intelligence won't help much unless you keep your house secure. Latest Articles. You might also like.

This topic is simply matchless :), it is pleasant to me.
I apologise, but, in my opinion, you are not right. I can defend the position. Write to me in PM, we will communicate.
I apologise, but, in my opinion, you commit an error. Write to me in PM.