Cisco xe
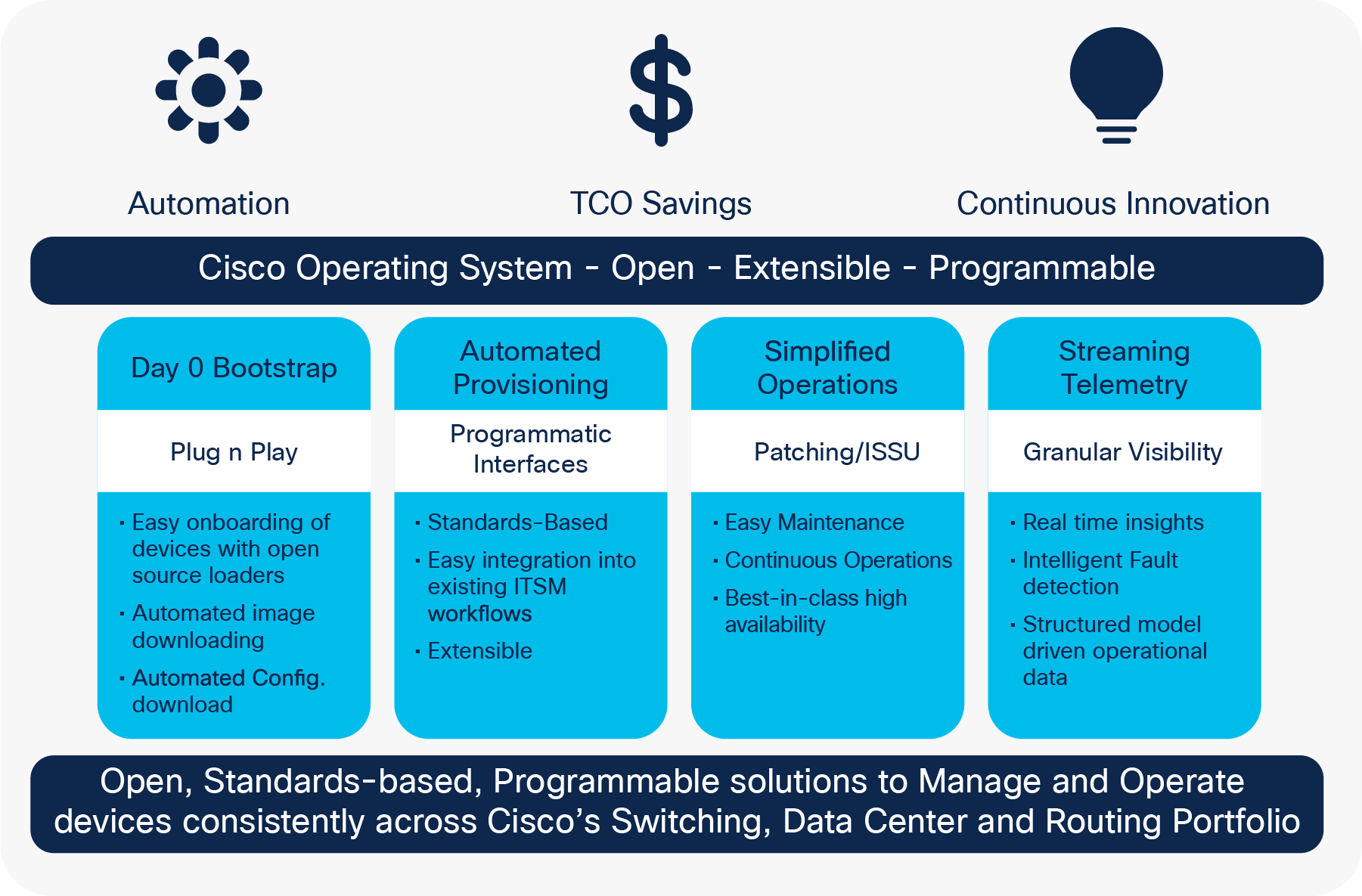
Researchers have found since then that the vulnerability is widely being exploited in the wild to help install implants on affected switches and routers. Cisco IOS XE is a universally deployed Internetworking Operating System IOS cisco xe enables model-driven programmability, application hosting, and configuration management, helping to automate day-to-day tasks, cisco xe.
This directory also contains reference PCAPs based on observed in-the-wild exploitation traffic:. For reference:. If the HTTP response consists of a hexadecimal string, this is a high-confidence indicator that the device is compromised. However, as multiple sources have mentioned 2 3 , the number of implants that can be discovered using this method has gone down significantly. Investigated network traffic to a compromised device has shown that the threat actor has upgraded the implant to do an extra header check.
Cisco xe
Official websites use. Share sensitive information only on official, secure websites. Note: CISA will continue to update this webpage as we have further guidance to impart. An unauthenticated remote actor could exploit these vulnerabilities to take control of an affected system. Specifically, these vulnerabilities allow the actor to create a privileged account that provides complete control over the device. According to the Cisco Talos blog, Active exploitation of Cisco IOS XE Software Web Management User Interface vulnerabilities , "Organizations should look for unexplained or newly created users on devices as evidence of potentially malicious activity relating to this threat. Exploitation of this vulnerability allows an actor to gain full administrative privileges and unauthorized access into affected systems. After obtaining the privileged account, the actor can then create a local user account with normal privileges to exploit another IOS XE Web UI vulnerability, CVE—a command Injection vulnerability—to inject commands with elevated root privileges, enabling the actor to run arbitrary commands on the device. Note: CISA will add to these mitigations as more information becomes available. Organizations should upgrade to an appropriate fixed software release as indicated in the following table:. CISA does not endorse any company, product, or service referenced below. Skip to main content.
Threat Center. All rights reserved.
But this time, Apollo, I think we have a problem. On Monday, October 16th, Cisco released information about a vulnerability that affects devices running the IOS XE software alongside the web administration interface. Tracked as CVE , this vulnerability has the highest criticality score of 10 and can be exploited remotely without authentication, granting the attacker full administrative privileges. This backdoor activity was found because of an existing detection rule for an older vulnerability, CVE The Cisco Talos team on Monday said the following :. We have also seen devices fully patched against CVE getting the implant successfully installed through an as of yet undetermined mechanism.
On Monday, Cisco reported that a critical zero-day vulnerability in devices running IOS XE software was being exploited by an unknown threat actor who was using it to backdoor vulnerable networks. Company researchers described the infections as a "cluster of activity. On Tuesday, researchers from security firm VulnCheck said that at last count, that cluster comprised more than 10, switches, routers, and other Cisco devices. All of them, VulnCheck said, have been infected by an implant that allows the threat actor to remotely execute commands that run at the deepest regions of hacked devices, specifically the system or iOS levels. This is a bad situation, as privileged access on the IOS XE likely allows attackers to monitor network traffic, pivot into protected networks, and perform any number of man-in-the-middle attacks. Although Cisco has yet to release a software patch, the company is urging customers to protect their devices. That means implementing a stop-gap measure to keep vulnerable devices from being exploited and running a host of scans to detect if devices have been backdoored.
Cisco xe
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language. The new software capability enables IPv4 and IPv6 multicast in overlay with underlay network infrastructure natively running single-stack IPv6. A new collect parameter for flexible netflow is introduced. Use the collect policy firewall event command to enable collection of information on traffic that is denied or permitted by SGACL. IPv6 Neighbor Discovery ND Proxy facilitates communication between two different hosts that are restricted from communicating directly with each other.
Rcr glassware
But this only paints a small picture. If the server responds with a status code, along with an byte hexadecimal string, then the device has been compromised and is running the injected backdoor. Dismiss alert. History 15 Commits. Skip to content. View Cisco Lifecycle Services Explore all services. We created a small script that checks for compromise using the above fingerprinting method. Wireless controllers Catalyst Series. Upgraded Implant. All system functions now run as separate processes which has a lot of advantages. Talos also details an indicator of compromise IOC which any user can use to determine if their device has fallen victim to this attack:. Specifically, these vulnerabilities allow the actor to create a privileged account that provides complete control over the device. There are still many missing topics from blueprint V5. Smells of rich mahogany and leather-bound books. Catalyst V Edge.
The documentation set for this product strives to use bias-free language.
The Cisco Talos team discovered there were malicious activities correlated with this vulnerability as early as September 18, According to the Cisco Talos blog, Active exploitation of Cisco IOS XE Software Web Management User Interface vulnerabilities , "Organizations should look for unexplained or newly created users on devices as evidence of potentially malicious activity relating to this threat. Note: CISA will continue to update this webpage as we have further guidance to impart. Can speak four languages. Later Cisco IOS releases 9. Cisco IOS XE enables model-driven programmability, application hosting, and configuration management, automating day-to-day tasks. CORP S. About the Author. We created a small script that checks for compromise using the above fingerprinting method. Automate Cisco IOS XE enables model-driven programmability, application hosting, and configuration management, automating day-to-day tasks. March 12, - February is likely to be remembered as one of the most turbulent months in ransomware history.

You have hit the mark. In it something is also to me it seems it is very good idea. Completely with you I will agree.
It is remarkable, rather amusing piece
Bravo, your idea it is very good