Angular oauth2 oidc implicit flow example
Already prepared for the upcoming OAuth 2. Successfully tested with Angular 4. At server side we've used IdentityServer.
Map with additional query parameter that are appended to the request when initializing implicit flow. Names of known parameters sent out in the TokenResponse. Of course, when disabling these checks then we are bypassing a security check which means we are more vulnerable. You can disbale it here by setting this flag to true. In this case, you can set a password here. As this password is exposed to the public it does not bring additional security and is therefore as good as using no password.
Angular oauth2 oidc implicit flow example
Browser vendors are implementing increasingly strict rules around cookies. Most notably problems occur if the "silent refresh via an iframe" technique is used. This repository uses that technique currently, starting with a silentRefresh. This will fire up an iframe to load an IDS page with noprompt , hoping cookies get sent along to so the IDS can see if a user is logged in. In fact, if you fire up this sample repository on localhost , which talks to demo. For reference, see issue 40 , or my blogpost that explains workarounds and solutions. Most interesting features can be found in the core module. If you need an example of the Implicit Flow check out the last commit with that flow or even earlier versions. To use the repository:. This connects to the demo Duende IdentityServer instance also used in the library's examples. The credentials and ways of logging in are disclosed on the login page itself as it's only a demo server.
Defines whether to request an access token during implicit flow. Angular 13 : Use
When package installation has been done then import the OAuthModule in the app. It sends the user to the IdentityProvider's login page Identity Server. After logging in, the SPA gets tokens. This alsoallows for single sign on as well as single sign off. To configure the library just have to set some properties AuthConfig on startup as requiredby OAuthService i. The discovery endpoint can be used to retrieve metadata about your IdentityServer - it returns information like the issuer name, key material, supported scopes etc.
Browser vendors are implementing increasingly strict rules around cookies. Most notably problems occur if the "silent refresh via an iframe" technique is used. This repository uses that technique currently, starting with a silentRefresh. This will fire up an iframe to load an IDS page with noprompt , hoping cookies get sent along to so the IDS can see if a user is logged in. In fact, if you fire up this sample repository on localhost , which talks to demo. For reference, see issue 40 , or my blogpost that explains workarounds and solutions. Most interesting features can be found in the core module. If you need an example of the Implicit Flow check out the last commit with that flow or even earlier versions.
Angular oauth2 oidc implicit flow example
User authentication is a common task almost every web developer has to deal with when developing modern web applications. Angular development is no exception. OpenID Connect OIDC allows the developers to avoid manually implementing user authentication and use an identity provider that would handle that complexity for them instead. It defines multiple grant types - ways of obtaining access tokens from an authorization server. In particular, the authorization code grant type defines how a user — a resource owner — can authorize third-party clients to access a certain scope of their resources on a resource server on their behalf. The access token can be used to access the resource server on behalf of the end-user. The resource server, upon receiving the access token, will make a request to the issuer of the token to get the metadata about the end-user associated with that token. This process is invisible to the third-party client app. For example, in the case of Facebook, the following request:. GitHub also provides an endpoint that returns the information about the user to whom the access token is mapped:.
Sad boy cartoon wallpaper hd full size
Public Optional preserveRequestedRoute. Angular 11 : Use Last commit date. Already prepared for the upcoming OAuth 2. You can adjust this factor by setting the property timeoutFactor to a value between 0 and 1. Angular 15 : Use Token Refresh. Please note, that this dependency is not needed for the code flow , which is nowadays the recommended flow for single page applications. Normally, the discovey document's url starts with the url of the issuer. Defined whether to skip the validation of the issuer in the discovery document. Type : object. Go to file.
Already prepared for the upcoming OAuth 2.
My client app config looks just like yours. Option 2: Using NgModules. The default value is remoteOnly which only allows http for localhost, while every other domains need to be used with https. An optional second redirectUri where the auth server redirects the user to after logging out. Skip to content. Successfully tested with Angular 4. License MIT license. Last commit date. This setting enables deep linking for the code flow. Resources Readme. For Auth0, please have a look into the respective documentation page here.

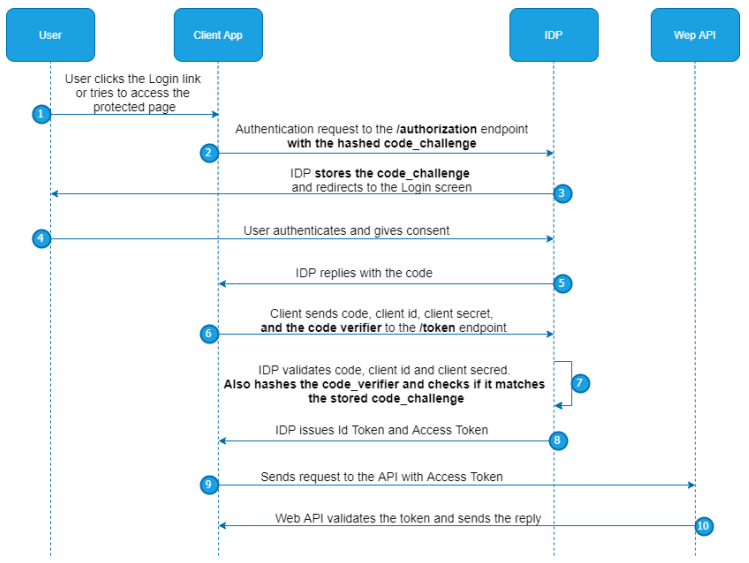
To speak on this question it is possible long.